Passwork: erinevus redaktsioonide vahel
| (ei näidata sama kasutaja 89 vahepealset redaktsiooni) | |||
| 13. rida: | 13. rida: | ||
Isanda veebikoht paistab selline |
Isanda veebikoht paistab selline |
||
| − | [[Fail:20250511-passwork-01.png| |
+ | [[Fail:20250511-passwork-01.png|1000px]] |
kus |
kus |
||
| 23. rida: | 23. rida: | ||
Väited |
Väited |
||
| − | * tundub, et tehniliselt on sama litsentsi võimalik kasutada nö kõrvutistes paigaldistes (kuna on toetatud offline kasutamine) |
+ | * tundub, et tehniliselt on sama litsentsi võimalik kasutada nö kõrvutistes paigaldistes (kuna on toetatud offline kasutamine) - nt taastetesti tegemiseks |
===Tööpõhimõte=== |
===Tööpõhimõte=== |
||
| 127. rida: | 127. rida: | ||
d20b50f94e42 passwork/docker-psmdb6 "/entrypoint.sh mong…" 1 second ago Up Less than a second 27017/tcp passwork_db |
d20b50f94e42 passwork/docker-psmdb6 "/entrypoint.sh mong…" 1 second ago Up Less than a second 27017/tcp passwork_db |
||
51053237c894 passwork/docker-php8.3 "/entrypoint.sh php-…" 1 second ago Up Less than a second passwork_php |
51053237c894 passwork/docker-php8.3 "/entrypoint.sh php-…" 1 second ago Up Less than a second passwork_php |
||
| + | </pre> |
||
| + | |||
| + | Tulemusena on moodustatud fail /srv/passwork/docker-compose.yaml ning selle alusel käivitatud konteinerid |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ docker compose ls |
||
| + | NAME STATUS CONFIG FILES |
||
| + | passwork running(5) /srv/passwork/docker-compose.yaml |
||
</pre> |
</pre> |
||
| 158. rida: | 166. rida: | ||
local passwork_db_data |
local passwork_db_data |
||
</pre> |
</pre> |
||
| + | |||
| + | ===Paigalduse lähtestamine=== |
||
Paigaldise lähtestamine, konteinerite kustamine |
Paigaldise lähtestamine, konteinerite kustamine |
||
| 193. rida: | 203. rida: | ||
Peale paigaldamist suundudes brauseriga teenuse url peale paistab selline pilt, valida keel, nt English |
Peale paigaldamist suundudes brauseriga teenuse url peale paistab selline pilt, valida keel, nt English |
||
| − | [[Fail:20250511-passwork-02.png| |
+ | [[Fail:20250511-passwork-02.png|1000px]] |
| − | seejärel paistab selline pilt |
+ | seejärel paistab selline pilt, esitada kontakt andmebaasiga (MongoDB) |
| − | [[Fail:20250511-passwork-03.png| |
+ | [[Fail:20250511-passwork-03.png|1000px]] |
| + | seejärel esitada litsents faili üles laadimise kujul |
||
| − | [[Fail:20250511-passwork-06.png|px800]] |
||
| + | |||
| + | [[Fail:20250511-passwork-04.png|1000px]] |
||
| + | |||
| + | seejärel kirjeldada esimene kasutaja, admin jms privileegidega |
||
| + | |||
| + | [[Fail:20250511-passwork-05.png|1000px]] |
||
| + | |||
| + | Lõpuks, peale sisselogimist paitsab selline pilt |
||
| + | |||
| + | [[Fail:20250511-passwork-06.png|1000px]] |
||
| + | |||
| + | ===https:// seadistsamine=== |
||
| + | |||
| + | https:// iseenesest töötab kohe algupäraselt, aga self-signed vms sertifikaadiga, custom sertifikaadi kasutamiseks sobib tekitada kaks faili |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ pwd |
||
| + | /srv/passwork |
||
| + | |||
| + | duser@pwrk-01:/srv/passwork$ ls -l conf/ssl/fullchain.pem conf/ssl/privkey.pem |
||
| + | -rw-r--r-- 1 duser root 3590 Jul 12 20:10 conf/ssl/fullchain.pem |
||
| + | -rw------- 1 duser root 1704 Jul 12 20:11 conf/ssl/privkey.pem |
||
| + | </pre> |
||
| + | |||
| + | ja öelda |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ docker compose stop |
||
| + | duser@pwrk-01:/srv/passwork$ docker compose start |
||
| + | </pre> |
||
| + | |||
| + | Tundub, et passwork rakendus sisaldab ise letsencrypt tuge kasutades docker-compose.yml failis, iseasi kui hea mõte on passwork rakendus teha internetist ligipääsetavaks |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ head -n 30 docker-compose.yaml |
||
| + | services: |
||
| + | nginx: |
||
| + | .. |
||
| + | environment: |
||
| + | - USE_LETSENCRYPT |
||
| + | - DOMAIN |
||
| + | ... |
||
| + | </pre> |
||
| + | |||
| + | Kindlasti on variant pidada eraldi nö sertifikaatide uuendamise nginx serveri ja sealt võtta sertifikaadid ja neid kasutada passwork dockerhostis |
||
| + | |||
| + | <pre> |
||
| + | # certbot certonly --manual --preferred-challenges=dns --email imre@auul.pri.ee --server https://acme-v02.api.letsencrypt.org/directory --agree-tos --cert-name pwrk.auul.pri.ee -d 'pwrk.auul.pri.ee' --key-type ecdsa |
||
| + | </pre> |
||
| + | |||
| + | ===Kasutajate haldamine=== |
||
| + | |||
| + | * Invite |
||
| + | |||
| + | ===2FA kasutamine=== |
||
| + | |||
| + | TODO |
||
| + | |||
| + | ===Kasutajate keskhaldus - LDAP kataloog=== |
||
| + | |||
| + | |||
| + | Väärtused |
||
| + | |||
| + | * Server - ldap://192.168.10.125 |
||
| + | * Service account -> Distinguished name (DN) - Administrator@dn.moraal.ee |
||
| + | * Service account -> Password - parool |
||
| + | * Service account -> Attribute name for login - samaccountname |
||
| + | |||
| + | ning pressida 'Test' - ootus on vastus 'Successfully logged in'. |
||
| + | |||
| + | Seejärel liikuda lahtri 'DN for finding users in AD/LDAP' juurde ja sisestada |
||
| + | |||
| + | dc=sise,dc=moraal,dc=ee |
||
| + | |||
| + | ja presside 'Refresh users', ootus on näha paneelis 'LDAP users' midagi sellist, '0/47 created'. Pressides View users näeb kataloogi sisu. |
||
| + | |||
| + | ===smtp teenusega integratsioon=== |
||
| + | |||
| + | smtp integratsiooni kasutatakse |
||
| + | |||
| + | * invite jaoks |
||
| + | |||
| + | smtp andmete kirjeldamiseks sobib liikuda |
||
| + | |||
| + | System settings -> Email service - Mailer config |
||
| + | |||
| + | ning kasutada nt selliseid väärtusi |
||
| + | |||
| + | * Sender's email - passwork@auul.pri.ee |
||
| + | * TODO |
||
===Kasutamine=== |
===Kasutamine=== |
||
| + | |||
| + | TODO |
||
| + | |||
| + | ===Haldusprotseduurid=== |
||
| + | |||
| + | * varundus ja taaste |
||
| + | * export ja import |
||
| + | |||
| + | ===Versiooni uuendmine - 7.0.8 -> 7.0.10=== |
||
| + | |||
| + | Eesmärgil lahendust uuendada, öeldakse kuid tulemusena saab muu hulgas sellise teksti konsoolile |
||
| + | |||
| + | <pre> |
||
| + | ./update.sh |
||
| + | |||
| + | .. |
||
| + | |||
| + | Backup successful |
||
| + | Unable to find image 'alpine:latest' locally |
||
| + | latest: Pulling from library/alpine |
||
| + | 9824c27679d3: Pull complete |
||
| + | Digest: sha256:4bcff63911fcb4448bd4fdacec207030997caf25e9bea4045fa6c8c44de311d1 |
||
| + | Status: Downloaded newer image for alpine:latest |
||
| + | ./update.sh: line 143: [[: 070008: value too great for base (error token is "070008") |
||
| + | No previous version is installed or version is below 070000. Code has been obtained, no need to recreate services during initial install. |
||
| + | duser@pwrk-01:/srv/passwork$ |
||
| + | </pre> |
||
| + | |||
| + | kus |
||
| + | |||
| + | * tundub, et süsteem kasutab alpine tõmmist mingiteks abistavateks tegevusteks |
||
| + | |||
| + | Siiski peale |
||
| + | |||
| + | <pre> |
||
| + | # cd /srv/paswork |
||
| + | # docker compose stop |
||
| + | # docker compose start |
||
| + | </pre> |
||
| + | |||
| + | on webgui pealt paista, et kasutatakse v. 7.0.10. Support vastas selle nähtuse kohta, et tarkvara uuendamine õnnestus ja nad kohendavad uuendamise osakonda. Tundub, et uuedamise käigus tõmmiseid endid ei asendatud, aga php konteinerite sees uuendati php rakenduse sisu. |
||
| + | |||
| + | Kasulikud lisamaterjalid |
||
| + | |||
| + | * https://docs.passwork.pro/b3vo-docker |
||
| + | |||
| + | ===Versiooni uuendmine - 7.0.10 -> 7.2.0=== |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ ./update.sh |
||
| + | Downloading version 070200... |
||
| + | % Total % Received % Xferd Average Speed Time Time Time Current |
||
| + | Dload Upload Total Spent Left Speed |
||
| + | 100 23.1M 100 23.1M 0 0 11.7M 0 0:00:01 0:00:01 --:--:-- 11.7M |
||
| + | Verified OK |
||
| + | Successfully checked signature for Passwork archive |
||
| + | WARN[0000] The "UID" variable is not set. Defaulting to a blank string. |
||
| + | WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string. |
||
| + | COMPOSE_PROFILES="local_notify,mongo" |
||
| + | WARN[0000] The "UID" variable is not set. Defaulting to a blank string. |
||
| + | WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string. |
||
| + | 2025-11-08T21:51:42.939+0000 writing admin.system.version to archive on stdout |
||
| + | 2025-11-08T21:51:42.940+0000 done dumping admin.system.version (1 document) |
||
| + | 2025-11-08T21:51:42.941+0000 writing pw.activity_logs to archive on stdout |
||
| + | 2025-11-08T21:51:42.941+0000 writing pw.snapshots to archive on stdout |
||
| + | 2025-11-08T21:51:42.941+0000 writing pw.tasks to archive on stdout |
||
| + | 2025-11-08T21:51:42.944+0000 writing pw.sessions to archive on stdout |
||
| + | 2025-11-08T21:51:42.951+0000 done dumping pw.sessions (247 documents) |
||
| + | |||
| + | .. |
||
| + | |||
| + | 2025-11-08T21:51:43.033+0000 done dumping pw.locks (0 documents) |
||
| + | 2025-11-08T21:51:43.034+0000 done dumping pw.ldap_users (0 documents) |
||
| + | Successfully copied 5.76MB to /srv/passwork/backup/ |
||
| + | WARN[0000] The "UID" variable is not set. Defaulting to a blank string. |
||
| + | WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string. |
||
| + | Backup successful |
||
| + | Container passwork_php Recreate |
||
| + | Container passwork_cron Recreate |
||
| + | Container passwork_php Recreated |
||
| + | Container passwork_nginx Recreate |
||
| + | Container passwork_cron Recreated |
||
| + | Container passwork_nginx Recreated |
||
| + | Container passwork_cron Starting |
||
| + | Container passwork_php Starting |
||
| + | Container passwork_php Started |
||
| + | Container passwork_nginx Starting |
||
| + | Container passwork_cron Started |
||
| + | Container passwork_nginx Started |
||
| + | Waiting for php-fpm and warming up. |
||
| + | Updated to 070200 successfully! |
||
| + | duser@pwrk-01:/srv/passwork$ docker ps |
||
| + | CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES |
||
| + | 3aabe1753ca3 passwork/docker-nginx "/entrypoint.sh ngin…" About a minute ago Up About a minute 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp passwork_nginx |
||
| + | eb1fa9a35ad0 passwork/docker-php8.3 "/entrypoint.sh tini…" About a minute ago Up About a minute passwork_cron |
||
| + | fb3a93ec5717 passwork/docker-php8.3 "/entrypoint.sh php-…" About a minute ago Up About a minute passwork_php |
||
| + | ced681df8cfb passwork/docker-postfix "/entrypoint.sh post…" 3 months ago Up 4 minutes 25/tcp passwork_postfix |
||
| + | 5c905a145c47 passwork/docker-psmdb6 "/entrypoint.sh mong…" 3 months ago Up 4 minutes 27017/tcp passwork_db |
||
| + | duser@pwrk-01:/srv/passwork$ |
||
| + | </pre> |
||
| + | |||
| + | Seejuures on veider, et jätkuvalt on mongodb versioon 6 |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ docker exec -it passwork_db mongosh |
||
| + | Current Mongosh Log ID: 6914a55f0239271dd7a762f8 |
||
| + | Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0 |
||
| + | Using MongoDB: 6.0.21-18 |
||
| + | Using Mongosh: 2.5.0 |
||
| + | ... |
||
| + | </pre> |
||
| + | |||
| + | St just põhjusel, et https://passwork.pro/blog/passwork-7-2/?ref=passwork.pro/blog aadressil tekst 'Release notes of 7.2.0' ütleb |
||
| + | |||
| + | 'Important: Passwork requires MongoDB version 7.0 or higher. Earlier versions are not supported and may cause compatibility issues.' |
||
| + | |||
| + | Võib-olla oleks õige sooritada selline järgnevus |
||
| + | |||
| + | # take backup of the virtaul machine of this dockerhost |
||
| + | # export at passwork webgui all content |
||
| + | # shut down system and prepare new clean dockerhost |
||
| + | # do fresh install using 7.2.0 software |
||
| + | # import previosly done export |
||
| + | # little bit of going over some configurations etc |
||
| + | |||
| + | ====MongoDB v. 6 -> v. 7 uuendamine==== |
||
| + | |||
| + | FCV väärtuse küsimine |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ docker exec -it passwork_db mongosh |
||
| + | Current Mongosh Log ID: 6917a020c571fefa92a762f8 |
||
| + | Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0 |
||
| + | Using MongoDB: 6.0.21-18 |
||
| + | Using Mongosh: 2.5.0 |
||
| + | |||
| + | For mongosh info see: https://www.mongodb.com/docs/mongodb-shell/ |
||
| + | |||
| + | ------ |
||
| + | The server generated these startup warnings when booting |
||
| + | 2025-11-14T21:31:05.489+00:00: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine. See http://dochub.mongodb.org/core/prodnotes-filesystem |
||
| + | 2025-11-14T21:31:05.967+00:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted. You can use percona-server-mongodb-enable-auth.sh to fix it |
||
| + | 2025-11-14T21:31:05.967+00:00: vm.max_map_count is too low |
||
| + | ------ |
||
| + | |||
| + | test> db.adminCommand( { getParameter: 1, featureCompatibilityVersion: 1 } ) |
||
| + | { featureCompatibilityVersion: { version: '6.0' }, ok: 1 } |
||
| + | </pre> |
||
| + | |||
| + | FCV muutmiseks sobib öelda mongosh promptis |
||
| + | |||
| + | <pre> |
||
| + | test> db.adminCommand( { setFeatureCompatibilityVersion: "7.0", confirm: true } ) |
||
| + | { ok: 1 } |
||
| + | </pre> |
||
| + | |||
| + | logis öeldakse |
||
| + | |||
| + | <pre> |
||
| + | {"t":{"$date":"2025-11-14T21:41:24.292+00:00"},"s":"I", "c":"-", "id":6744302, "ctx":"conn13","msg":"setFeatureCompatibilityVersion succeeded","attr":{"upgradeOrDowngrade":"upgrade","serverType":"replica set/standalone","fromVersion":"6.0","toVersion":"7.0"}} |
||
| + | </pre> |
||
| + | |||
| + | ===Versiooni uuendmine - 7.2.3 -> 7.2.4=== |
||
| + | |||
| + | Tundub, et 7.2.x osakonnas toimuvad mõnda aega uuendused nö ootuspäraselt, st pole vaja tegeleda eraldi andmebaasiga, ei ole muidu tagasilööke jne |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:/srv/passwork$ ./update.sh |
||
| + | ... |
||
| + | </pre> |
||
| + | |||
| + | ===Infoarhitektuur=== |
||
| + | |||
| + | Väited |
||
| + | |||
| + | * Kõige peamisem andmete salvestamise nö konteiner on 'vault' |
||
| + | * Kasutaja saab vaikimisi moodustada vaultisid, kui ta neis olevatele saladustele ligipääsu teistega ei jaga, jääb vault privaateseks |
||
| + | * Passwork kasutajaid saab organiseerida gruppidesse (user group ehk ug-) |
||
| + | |||
| + | Passwork sisu hieraria on selline |
||
| + | |||
| + | <pre> |
||
| + | Vault-1 Vault-2 |
||
| + | | | |
||
| + | | | |
||
| + | | | |
||
| + | |----- Folder-1-a |---- Folder-2-a |
||
| + | | | | | |
||
| + | | | | | |
||
| + | | |----- Password-1-a-1 | |----- Password-2-a-1 |
||
| + | | |----- Password-1-a-2 | |----- Password-2-a-2 |
||
| + | | ... | ... |
||
| + | | | ... |
||
| + | | |
||
| + | |----- Folder-1-b |
||
| + | | |
||
| + | | |
||
| + | |----- Password-1-b-1 |
||
| + | | ... |
||
| + | | |
||
| + | |----- Password-1-b-2 |
||
| + | | |
||
| + | | |
||
| + | |---- Name-1-b-2-a |
||
| + | |---- Login-1-b-2-a |
||
| + | |---- Password-1-b-2-a |
||
| + | |---- URL-1-b-2-a |
||
| + | | ... |
||
| + | | |
||
| + | |---- Name-1-b-2-b |
||
| + | |---- Login-1-b-2-b |
||
| + | |---- Password-1-b-2-b |
||
| + | |---- URL-1-b-2-b |
||
| + | ... |
||
| + | |||
| + | |||
| + | </pre> |
||
| + | |||
| + | * Passwork 'Password' sissekande field on kõige elementaarsem info esinemise element |
||
| + | |||
| + | Kontseptuaalselt võiks passwork lahendust kasutada sellise mõtlemisega |
||
| + | |||
| + | * folderite abil moodustatakse ressrusside parvi (nt rg-infosysteem-yks, rg-infosysteem-kaks, rg-pve, rg-tulemyyr, rg-storage) |
||
| + | * kasutajate gruppide abil moodustatakse kasutajate parvi (nt ug-is-yks-sysadm, ug-is-yks-appadm, ug-is-yks-user, ug-pve-sysadm, ug-storage-sysadm) |
||
| + | * passwork acl süsteemi abil ühendatakse ressurside ja gruppide parvi omavahel kokku |
||
| + | |||
| + | ressursside-infovarade-infosüsteemide paigutamine kolme dimensiooni |
||
| + | |||
| + | * internal vs external dimensioon - kas kasutajad on eranditult haldusüksusest või tegemist on internetti publitseeritud teenusega |
||
| + | * core vs leaf dimensioon - kas tegemist on tuum teenusega, st teenusega mis ei sõltu millestki muust (nt kettakast); või on tegemist paljudest komponentidest sõltuva lahendusega (nt lõppkasutajate teenindav infosüsteem avalikus internetis (sõltub kettakastist, virtualiseerimise platvormist, tulemüürist) |
||
| + | * prod-test-dev dimensioon - kas tegu on toodangu või test kasutusjuhtumiga infosüsteemist |
||
| + | |||
| + | Nt võiks kasutada selliseid vault nimesid |
||
| + | |||
| + | * vlt-core-int-prod - sisemise publiku kasutamiseks tuum ressruss - nt kettakast |
||
| + | * vlt-core-ext-prod - avalikuks kasutamiseks tuum ressurss - sellist kombinatsiooni esineb nö looduses harva |
||
| + | * vlt-leaf-ext-prod - avalikuks kasutamiseks mõeldud infosüsteem - nt mingit sorti wordpress/drupal/mediawiki põhine avalik lahendus |
||
| + | * vlt-leaf-int-prod - sisemiseks kasutamiseks mõeldud infosüsteem - nt ipam halduslahendus |
||
| + | * vtl-leaf-ext-test - avalikuks testimiseks mõeldud infosüsteem - nt mingit sorti wordpress/drupal/mediawiki põhine avalik lahendus |
||
| + | |||
| + | Kusjuures dimensioonidele kombinatsioonidele vastavad erinevad vault'id. |
||
| + | |||
| + | Sellise lähenemise tulemusena on võimalik erinevatele passwork kasutajatele usaldada ligipääse erinevatele ressurssidele suhteliselt üksikajalikult ligipääsemisi kontrollides, nt |
||
| + | |||
| + | * ug-storage-sysadm - storage ressurssidele (füüsilise kettakasti haldusliides, ceph lahenduse node'id) saavad ligi süsteemiadministreerimise tegevuste asjus gruppi kuuluvad kasutajad (ja ega sellise ligipääsuga ei saagi eriti muud toimuda peale süsteemiadministreerimise, nt lun tekitamine, lun group seadistamine, host affinity kirjeldamine) |
||
| + | * rg-storage - storage ressursside gruppi kuuluvad Password sissekanded asuvad vastavas folderis |
||
| + | * kuigi nö tehniliselt saaks anda rg-storage resource-grupile ligipääse nt ug-is-yks-sysadm kasutajatele grupile, vaevalt see on kuigi asjakohane |
||
| + | |||
| + | Esmalt moodustatakse kasutajate grupp, antud juhul on vaatluse all grupp 'ug-pve-sysadm' |
||
| + | |||
| + | * grupis on üks kasutaja, algustähega M |
||
| + | * grupp on seotud ühele vaultile ligipääsemisega |
||
| + | * grupi nime võiks lugeda selliselt, et pve lahendusele soovitakse anda süsteemi-administreerimise alast ligipääsu |
||
| + | |||
| + | [[Fail:20250727-passwork-rg-ug-01.png|1300px]] |
||
| + | |||
| + | seejärel: |
||
| + | |||
| + | * seostatakse kasutajate grupiga kasutaja Mart Kask - paremal üleval 'USERS' |
||
| + | * seostatakse kasutajate grupiga ressursside grupp 'vlt-core-int-prod -> rg-pve', millele antakse ligipääs tasemel 'Administrator' |
||
| + | |||
| + | [[Fail:20250727-passwork-rg-ug-03.png|1300px]] |
||
| + | |||
| + | Tulemus paistab sedasi |
||
| + | |||
| + | * avatud on ressurside vaates 'vlt-core-int-prod -> rg-pve' osakond, ning Password tüüpi sissekanne 'pve-svc-02.auul.pri.ee' |
||
| + | * sissekande koosseisus on muude field'ide hulgas 'pve totp' nimega field, mille omadus on olla nö google authenticator compatible time-based-on-time-password |
||
| + | * eraldi on lisaks avatud pop-up aken pressides üleval 'Access to folder -> 2 users' peale, kust on näha millise grupp abil on mis privleeg antud |
||
| + | |||
| + | [[Fail:20250727-passwork-rg-ug-02.png|1300px]] |
||
| + | |||
| + | ===MongoDB=== |
||
| + | |||
| + | <pre> |
||
| + | duser@pwrk-01:~$ docker exec -it passwork_db mongosh |
||
| + | Current Mongosh Log ID: 6886ca4e9e57fe6db9a762f8 |
||
| + | Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0 |
||
| + | Using MongoDB: 6.0.21-18 |
||
| + | Using Mongosh: 2.5.0 |
||
| + | |||
| + | For mongosh info see: https://www.mongodb.com/docs/mongodb-shell/ |
||
| + | ... |
||
| + | |||
| + | pw> show dbs |
||
| + | admin 40.00 KiB |
||
| + | config 108.00 KiB |
||
| + | local 72.00 KiB |
||
| + | pw 5.72 MiB |
||
| + | pw> |
||
| + | |||
| + | test> use pw |
||
| + | switched to db pw |
||
| + | pw> db.items.countDocuments() |
||
| + | 193 |
||
| + | pw> |
||
| + | </pre> |
||
| + | |||
| + | vault andmete küsimine |
||
| + | |||
| + | <pre> |
||
| + | pw> db.vaults.find({ name: /v-auul/i }) |
||
| + | [ |
||
| + | { |
||
| + | _id: ObjectId('68729adc05fb74f7b20f9ee6'), |
||
| + | createdAt: ISODate('2025-07-12T17:26:52.534Z'), |
||
| + | creatorId: ObjectId('68729a5c6515f0d969054e06'), |
||
| + | deleted: null, |
||
| + | isSnapshotsMigrated: true, |
||
| + | isUsersMigrated: true, |
||
| + | masterKeyHash: null, |
||
| + | name: 'v-auul', |
||
| + | salt: null, |
||
| + | updatedAt: ISODate('2025-07-12T21:40:47.599Z') |
||
| + | } |
||
| + | ] |
||
| + | pw> |
||
| + | </pre> |
||
| + | |||
| + | Folder info küsimine |
||
| + | |||
| + | <pre> |
||
| + | pw> db.folders.find({ "name": /rg-pve/i }).pretty() |
||
| + | [ |
||
| + | { |
||
| + | _id: ObjectId('68865a19531c35bd9306be7b'), |
||
| + | ancestorIds: [], |
||
| + | createdAt: ISODate('2025-07-27T16:55:53.214Z'), |
||
| + | deleted: null, |
||
| + | name: 'rg-pve', |
||
| + | updatedAt: ISODate('2025-07-27T16:55:53.214Z'), |
||
| + | vaultId: ObjectId('68865953a9c423aa79042ef2') |
||
| + | } |
||
| + | ] |
||
| + | pw> |
||
| + | </pre> |
||
| + | |||
| + | Praktiliselt sisu sissekannetega ei saa sellisel viisil töötada, kuna sisu-andmed on krüptitud. |
||
| + | |||
| + | ===API kasutamine=== |
||
| + | |||
| + | Kasutuskoha ettevalmistamine |
||
| + | |||
| + | <pre> |
||
| + | root@dh-passwork-test:~# apt install python3-venv |
||
| + | root@dh-passwork-test:~# su - imre |
||
| + | imre@dh-passwork-test:~$ python3 -m venv ~/myenv |
||
| + | imre@dh-passwork-test:~$ source ~/myenv/bin/activate |
||
| + | (myenv) imre@dh-passwork-test:~$ pip install git+https://github.com/passwork-me/passwork-python.git |
||
| + | |||
| + | (myenv) imre@dh-passwork-test:~$ pip list |
||
| + | Package Version |
||
| + | ------------------ --------- |
||
| + | certifi 2025.7.14 |
||
| + | cffi 1.17.1 |
||
| + | charset-normalizer 3.4.2 |
||
| + | cryptography 45.0.5 |
||
| + | idna 3.10 |
||
| + | passwork-python 0.1.3 |
||
| + | pbkdf2 1.3 |
||
| + | pip 24.0 |
||
| + | pycparser 2.22 |
||
| + | python-dotenv 1.1.1 |
||
| + | requests 2.32.4 |
||
| + | urllib3 2.5.0 |
||
| + | </pre> |
||
| + | |||
| + | API võtme tekitamine |
||
| + | |||
| + | * peale sisselogimist 5 minuti jooksul liikuda kasutaja 'Authorization and 2FA' osakonda |
||
| + | * liikuda sektsiooni 'API tokens' juurde |
||
| + | * pressida Generate ja salvestada kaks saladust, neid on pärast python skriptis tarvis |
||
| + | |||
| + | Kasutamine |
||
| + | |||
| + | <pre> |
||
| + | $ cat pwrk-02.py |
||
| + | import json |
||
| + | from passwork_client import PassworkClient |
||
| + | |||
| + | client = PassworkClient(host="https://pwrk.auul.pri.ee/") |
||
| + | client.set_tokens("uUQUMutd9VNuAFQ8Vu8RswPDV0JIO0Q+tl1b2uF9jpU=", "lnuTB/xbE3D+VV6b5+/bn+lrTR5A04x7BIVayfx3eG8=") |
||
| + | |||
| + | vault_name = "vlt-test-02" |
||
| + | vault_id = client.create_vault(vault_name) |
||
| + | print(f"Vault was created: {vault_id}") |
||
| + | </pre> |
||
| + | |||
| + | ning käivitamisel |
||
| + | |||
| + | <pre> |
||
| + | (myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py |
||
| + | Vault was created: 6887d71da0f06ae02f060419 |
||
| + | </pre> |
||
| + | |||
| + | Alternatiiv 'client.create_vault' väljendusele on kasutada 'client.call' kuju, nt on samaväärne eelmisele esitada |
||
| + | |||
| + | <pre> |
||
| + | .. |
||
| + | vault_name = "vlt-test-02" |
||
| + | vault_id = client.call("POST", "/api/v1/vaults", { |
||
| + | "name": vault_name |
||
| + | }) |
||
| + | |||
| + | print (vault_id) |
||
| + | ... |
||
| + | </pre> |
||
| + | |||
| + | Olemasolvate vaultide nimekirja saamine |
||
| + | |||
| + | <pre> |
||
| + | .. |
||
| + | vaults = client.call("GET", "/api/v1/vaults") |
||
| + | print(json.dumps(vaults, indent=2)) |
||
| + | ... |
||
| + | |||
| + | (myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py |
||
| + | { |
||
| + | "items": [ |
||
| + | { |
||
| + | "id": "78864af6acf14cf24a0472aa", |
||
| + | "name": "vlt-core-ext-prod", |
||
| + | "hasFolders": true, |
||
| + | "isGranted": true, |
||
| + | "isVisible": true |
||
| + | }, |
||
| + | { |
||
| + | "id": "78864af6acf14cf24a0472b9", |
||
| + | "name": "vlt-core-ext-test", |
||
| + | "hasFolders": false, |
||
| + | "isGranted": true, |
||
| + | "isVisible": true |
||
| + | }, |
||
| + | .. |
||
| + | </pre> |
||
| + | |||
| + | entry tekitamise näide |
||
| + | |||
| + | <pre> |
||
| + | import json |
||
| + | from passwork_client import PassworkClient |
||
| + | |||
| + | client = PassworkClient(host="https://pwrk.auul.pri.ee/") |
||
| + | client.set_tokens("uUQUMutd9VNuAFQ8Vu8RswPDV0JIO0Q+tl1b2uF9jpU=", "lnuTB/xbE3D+VV6b5+/bn+lrTR5A04x7BIVayfx3eG8=") |
||
| + | |||
| + | vault_name = "vlt-test-02" |
||
| + | vault_id = client.create_vault(vault_name) |
||
| + | print (vault_id) |
||
| + | |||
| + | folder_id_01 = client.call("POST", "/api/v1/folders", { |
||
| + | "vaultId": vault_id, |
||
| + | "name": "rg-fld-01" |
||
| + | }) |
||
| + | |||
| + | print (folder_id_01) |
||
| + | |||
| + | folder_id_02 = client.call("POST", "/api/v1/folders", { |
||
| + | "vaultId": vault_id, |
||
| + | "name": "rg-fld-02" |
||
| + | }) |
||
| + | |||
| + | print (folder_id_02) |
||
| + | |||
| + | entry_01 = client.call("POST", "/api/v1/items", { |
||
| + | "vaultId": vault_id, |
||
| + | "folderId": folder_id_02["id"], |
||
| + | "name": "entry_01", |
||
| + | "login": "login_01", |
||
| + | "url": "https://login_01.url/" |
||
| + | }); |
||
| + | |||
| + | entry_02 = client.call("POST", "/api/v1/items", { |
||
| + | "vaultId": vault_id, |
||
| + | "folderId": folder_id_02["id"], |
||
| + | "name": "entry_02", |
||
| + | "login": "login_02", |
||
| + | "url": "https://login_02.url/" |
||
| + | }); |
||
| + | |||
| + | entries = client.call("GET", "/api/v1/items", { |
||
| + | "vaultId": vault_id, |
||
| + | "folderId": folder_id_02["id"] |
||
| + | }); |
||
| + | |||
| + | print(json.dumps(entries, indent=2)) |
||
| + | |||
| + | |||
| + | (myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py |
||
| + | 6887e42b11d60d12790a962e |
||
| + | {'id': '6887e42bda4e92f70107ca2a'} |
||
| + | {'id': '6887e42b5f680d552109df55'} |
||
| + | { |
||
| + | "items": [ |
||
| + | { |
||
| + | "id": "6887e42ba3189a9a790e08ab", |
||
| + | "name": "entry_01", |
||
| + | "folderId": "6887e42b5f680d552109df55", |
||
| + | "vaultId": "6887e42b11d60d12790a962e", |
||
| + | "isDeleted": false, |
||
| + | "login": "login_01", |
||
| + | "url": "https://login_01.url/", |
||
| + | "tags": [], |
||
| + | "color": 0, |
||
| + | "isFavorite": false |
||
| + | }, |
||
| + | { |
||
| + | "id": "6887e42ba0f06ae02f060429", |
||
| + | "name": "entry_02", |
||
| + | "folderId": "6887e42b5f680d552109df55", |
||
| + | "vaultId": "6887e42b11d60d12790a962e", |
||
| + | "isDeleted": false, |
||
| + | "login": "login_02", |
||
| + | "url": "https://login_02.url/", |
||
| + | "tags": [], |
||
| + | "color": 0, |
||
| + | "isFavorite": false |
||
| + | } |
||
| + | ] |
||
| + | } |
||
| + | (myenv) imre@dh-passwork-test:~$ |
||
| + | </pre> |
||
| + | |||
| + | Kasulikud lisamaterjalid |
||
| + | |||
| + | * https://docs.passwork.pro/api-and-integrations |
||
| + | * paigalduse koosseisus on hea .pdf fail |
||
| + | |||
| + | <pre> |
||
| + | root@dh-passwork-test:~# find /srv/passwork/ -name \*reference.pdf -ls |
||
| + | 1835842 1312 -rw-r--r-- 1 duser duser 1340005 Jul 19 15:10 /srv/passwork/www/070009/files/api-schema/Api\ reference.pdf |
||
| + | root@dh-passwork-test:~# |
||
| + | </pre> |
||
| + | |||
| + | ===brauseri plugin=== |
||
| + | |||
| + | Väited |
||
| + | |||
| + | * kõige tavalisem viis passwork kasutamiseks parooli sisestuse olukorras on avatud nt kõrvuti kaks brauserit: 1. passwork kust vaadatakse saladus, 2. veebikoht kuhu pastetakse saladus |
||
| + | * brauseri plugin abil aitab passwork vastata brauseril ligipääsu küsimustele automaatselt (veebikohtade autentimise vorme automaatselt täites, eriti username ja password, vähem totp) |
||
| + | * brauseri plugina aktiveerimisel moodustatakse brauseri ja passwork vahele api key laadse usalduse kasutamise sarnane kontakt |
||
| + | * ühelt poolt on brauseri pöördumise võimekus registreeritud passwork'is |
||
| + | * teiselt poolt on passwork asukoht ja vajalik credential registreeritud brauseris (local storage vms osakonnas) |
||
| + | * passwork kasutamine brauseris kasutada olevate paroolide jaoks ei eelda, et sama brauseriga on passwork rakendusse sisse logitud, st see toimub taustal |
||
| + | |||
| + | ====brauseri plugina paigaldamine==== |
||
| + | |||
| + | * https://passwork.pro/user-guides/browser-extension/getting-started |
||
| + | * https://chromewebstore.google.com/detail/passwork-self-hosted/ibiipnmmlnehmeonnhbdajcfagcgihkl |
||
| + | |||
| + | google chrome web store |
||
| + | |||
| + | [[Fail:20250914-passwork-chrome-plugin-02.png|900px]] |
||
| + | |||
| + | plugina ühendamine passwork self-hosted lahendusega, Host lahtrisse tuleb kirjutada nt https://pwrk.auul.pri.ee/ |
||
| + | |||
| + | [[Fail:20250914-passwork-chrome-plugin-03.png|1100px]] |
||
| + | |||
| + | Lõpuks öeldakse 'Extension is authorized' (tõenäoliselt küsitakse passwork veebikoha ligipääsu ka). Edaspidi kasutamise ajal ei ole sama brauseriga sisselogimine eelduseks. |
||
| + | |||
| + | ====brauseri plugina kasutamine==== |
||
| + | |||
| + | Kasutamine paistab välja selline |
||
| + | |||
| + | [[Fail:20250801-passwork-brauser-01.png|1000px]] |
||
| + | |||
| + | kus |
||
| + | |||
| + | * brauseri aadressi real on paremal pluginate-extensionite osakond, eriti passwork lisa |
||
| + | * antud juhul seisneb teravmeelsus selles, et passwork'i logitakse sisse sama passwork abil |
||
| + | |||
| + | ====brauseri plugina uuendamine==== |
||
| + | |||
| + | Tundub, et uuendamine toimub MacOS keskkonnas töötava Google Chrome puhul nö automaatselt brauseri enda uuendamise käigus, maksab episoodiliselt üle kontrollida. |
||
===Kasulikud lisamaterjalid=== |
===Kasulikud lisamaterjalid=== |
||
Viimane redaktsioon: 16. detsember 2025, kell 07:11
Sissejuhatus
TODO
Olulised veebikohad
- https://passwork.pro/ - põhiveebikoht
- https://portal.passwork.pro/ - saab tarkvara kopeerida eeldusel, et on ostetud vms passwork kasutamise voli
- https://docs.passwork.pro/ - dokumentatsioon
Tarkvara ost
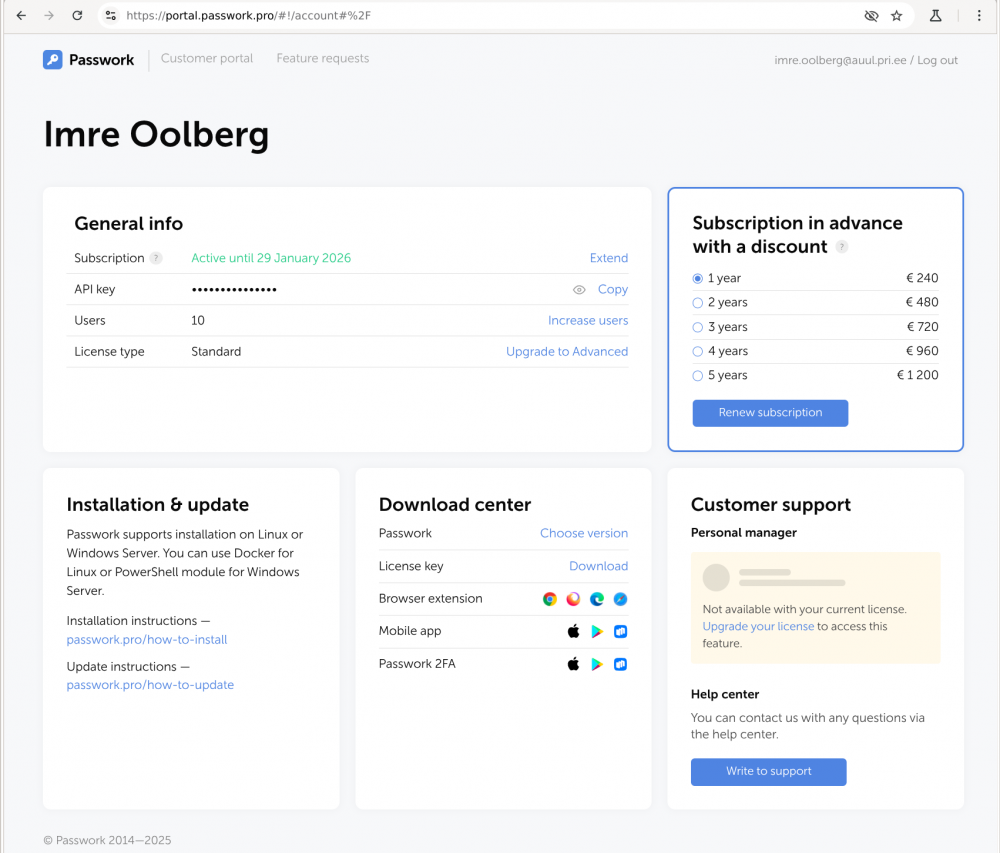
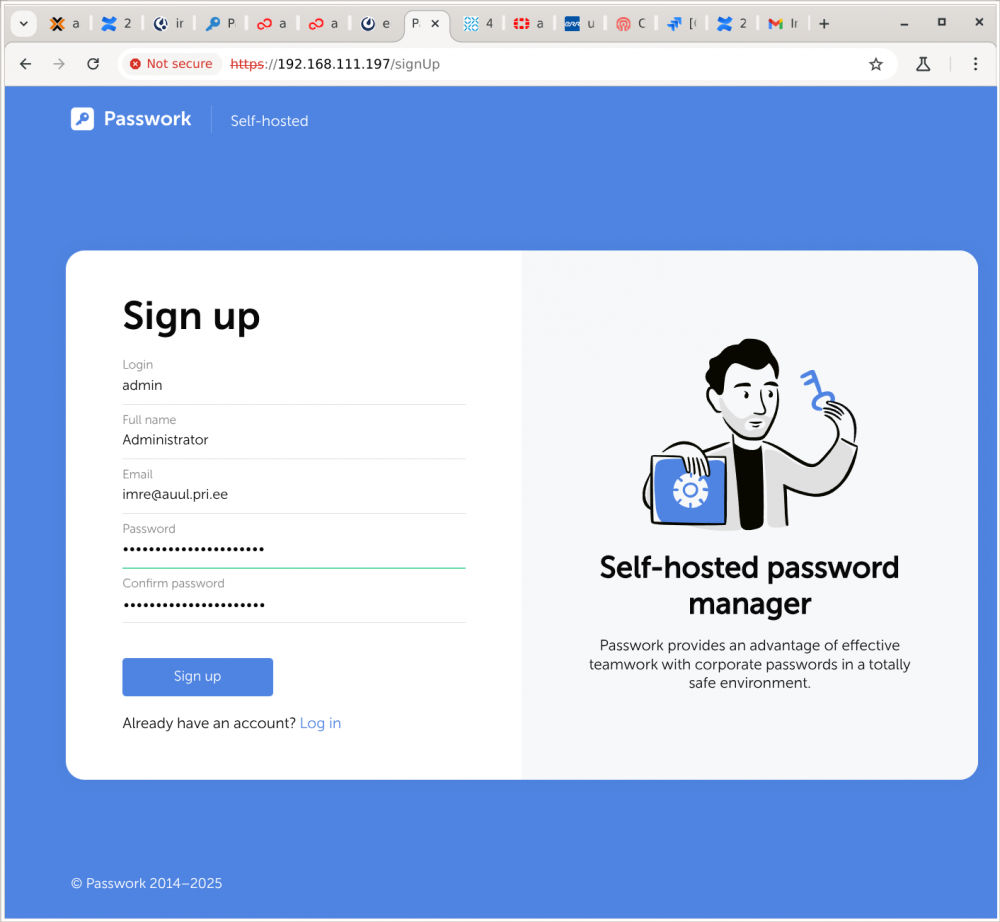
Isanda veebikoht paistab selline
kus
- API key - seda sõne väärtust küsitakse paigaldamise käigus, st tundub, et selle alusel kopeeritakse repost tarkvara
- License key - see fail tuleb üles laadida üks kord esimesel lahenduse käivitamisel
- Passwork - Choose version - saab alla laadida tarkvara meelepärase versiooni .zip arhiivi
Väited
- tundub, et tehniliselt on sama litsentsi võimalik kasutada nö kõrvutistes paigaldistes (kuna on toetatud offline kasutamine) - nt taastetesti tegemiseks
Tööpõhimõte
passwork lahendust saab kasutada mitmel viisil kohepeal paigaldades
- passwork paigaldus - docker konteiner põhiselt
- passwork paigaldus - tava-operatsiooni põhiselt
- passwork paigaldus ilma internetii ühtendamata arvutis
- passwork paigaldus internetti ühendutud arvutis
Käesolevas tekstis tegeledakse sellise kombinatsiooniga
- docker põhine
- arvutil on ühendus internetiga
Ettevalmistamine
Nt selline Docker CE tarkvara põhinev Ubuntu 24.04 dockerhost sobib kasutamiseks
duser@pwrk-01:/srv/passwork$ df -t ext4 -T -h Filesystem Type Size Used Avail Use% Mounted on /dev/mapper/system-root ext4 14G 2.8G 11G 21% / /dev/mapper/vg_data-var_lib_docker ext4 5.9G 2.1G 3.5G 38% /var/lib/docker /dev/mapper/vg_data-srv ext4 5.9G 4.2G 1.4G 76% /srv
Paigaldamine
passwork lahenduse paigaldamine võiks toimuda nt selliselt
duser@pwrk-01:~# su - duser
duser@pwrk-01:~$ cd /srv/passwork
duser@pwrk-01:/srv/passwork$
duser@pwrk-01:/srv/passwork$ wget https://repos.passwork.pro/repository/docker/passwork_compose_install.sh
duser@pwrk-01:/srv/passwork$ chmod +x passwork_compose_install.sh
duser@pwrk-01:/srv/passwork$ ./passwork_compose_install.sh
duser@pwrk-01:/srv/passwork$ ./passwork_compose_install.sh
Portal Passwork is available from your host. Online mode.
Docker version is 18.06 or higher
Docker Compose plugin is installed
User is either root or in the docker group
Checking if system is using supported package manager
Using apt-get to install packages
All required packages are already installed
Enter Portal API key: T16Ifdq10RXhaYlOlzFm1ZcPxcP4v4fMSDlvK3zSmeMzD1aRBSO4Y....
Valid Portal API key entered: T16Ifdq10RXhaYlOlzFm1ZcPxcP4v4fMSDlvK3zSmeMzD1aRBSO4Y....
Portal API key is correct
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 64054 100 64054 0 0 247k 0 --:--:-- --:--:-- --:--:-- 247k
Files downloaded and unpacked successfully
.env file created successfully
Running update: ./update.sh
Downloading version 070002...
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 22.4M 100 22.4M 0 0 9787k 0 0:00:02 0:00:02 --:--:-- 9785k
Verified OK
Successfully checked signature for Passwork archive
time="2025-05-11T16:46:41Z" level=warning msg="The \"UID\" variable is not set. Defaulting to a blank string."
time="2025-05-11T16:46:41Z" level=warning msg="The \"DB_RUN_FLAGS\" variable is not set. Defaulting to a blank string."
No previous version is installed or version is below 070000. Code has been obtained, no need to restart services during initial install.
Already copied
=== INSTALLED ===
time="2025-05-11T16:46:41Z" level=warning msg="The \"DB_RUN_FLAGS\" variable is not set. Defaulting to a blank string."
time="2025-05-11T16:46:41Z" level=warning msg="The \"UID\" variable is not set. Defaulting to a blank string."
Network passwork_passwork Creating
Network passwork_passwork Created
Container passwork_cron Creating
Container passwork_db Creating
Container passwork_php Creating
Container passwork_php Created
Container passwork_nginx Creating
Container passwork_db Created
Container passwork_cron Created
Container passwork_nginx Created
Container passwork_postfix Creating
Container passwork_postfix Created
Container passwork_php Starting
Container passwork_cron Starting
Container passwork_db Starting
Container passwork_db Started
Container passwork_cron Started
Container passwork_php Started
Container passwork_nginx Starting
Container passwork_nginx Started
Container passwork_postfix Starting
Container passwork_postfix Started
Started successfully
Please check running containers
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
c13dcc5f926d passwork/docker-postfix "/entrypoint.sh post…" 1 second ago Up Less than a second 25/tcp passwork_postfix
c86ecb29c606 passwork/docker-nginx "/entrypoint.sh ngin…" 1 second ago Up Less than a second 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp passwork_nginx
395b835b2853 passwork/docker-php8.3 "/entrypoint.sh tini…" 1 second ago Up Less than a second passwork_cron
d20b50f94e42 passwork/docker-psmdb6 "/entrypoint.sh mong…" 1 second ago Up Less than a second 27017/tcp passwork_db
51053237c894 passwork/docker-php8.3 "/entrypoint.sh php-…" 1 second ago Up Less than a second passwork_php
Tulemusena on moodustatud fail /srv/passwork/docker-compose.yaml ning selle alusel käivitatud konteinerid
duser@pwrk-01:/srv/passwork$ docker compose ls NAME STATUS CONFIG FILES passwork running(5) /srv/passwork/docker-compose.yaml
Tulemusena on kopeeritud sellised tõmmised
duser@pwrk-01:/srv/passwork$ docker image ls REPOSITORY TAG IMAGE ID CREATED SIZE passwork/docker-nginx latest ad5af3d7b172 3 days ago 195MB passwork/docker-php8.3 latest 90f5ff5ecfa1 12 days ago 563MB passwork/docker-postfix latest cd30c223cfc1 4 weeks ago 150MB passwork/docker-psmdb6 latest b055d5d4f764 2 months ago 831MB
Tulemusena on moodustatud selline võrk
duser@pwrk-01:/srv/passwork$ docker network ls NETWORK ID NAME DRIVER SCOPE c294d961e9b9 bridge bridge local ef6c4241d0ae host host local 0652ad4a8546 none null local e1d94f16ffcf passwork_passwork bridge local
Tulemusena on tekitatud selline volume
duser@pwrk-01:/srv/passwork$ docker volume ls DRIVER VOLUME NAME local passwork_db_data
Paigalduse lähtestamine
Paigaldise lähtestamine, konteinerite kustamine
duser@pwrk-01:/srv/passwork$ docker compose down WARN[0000] The "UID" variable is not set. Defaulting to a blank string. WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string. [+] Running 6/6 ✔ Container passwork_db Removed 0.1s ✔ Container passwork_cron Removed 0.5s ✔ Container passwork_postfix Removed 0.1s ✔ Container passwork_nginx Removed 0.1s ✔ Container passwork_php Removed 0.1s ✔ Network passwork_passwork Removed
Named volume kustutamine
duser@pwrk-01:/srv/passwork$ docker volume rm passwork_db_data passwork_db_data
Failisüsteemi osa kustutamine
root@pwrk-01:/srv/passwork# rm -rf .env .env.example *
root@pwrk-01:/srv/passwork# find -ls
12 4 drwxr-xr-x 2 duser duser 4096 May 11 17:02 .
Esmakordne käivitamine
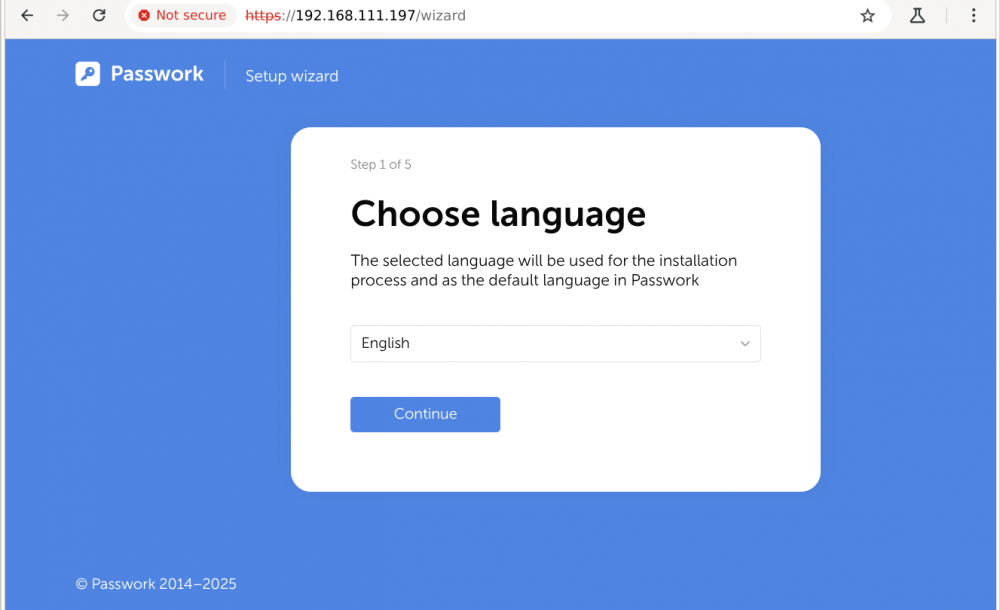
Peale paigaldamist suundudes brauseriga teenuse url peale paistab selline pilt, valida keel, nt English
seejärel paistab selline pilt, esitada kontakt andmebaasiga (MongoDB)
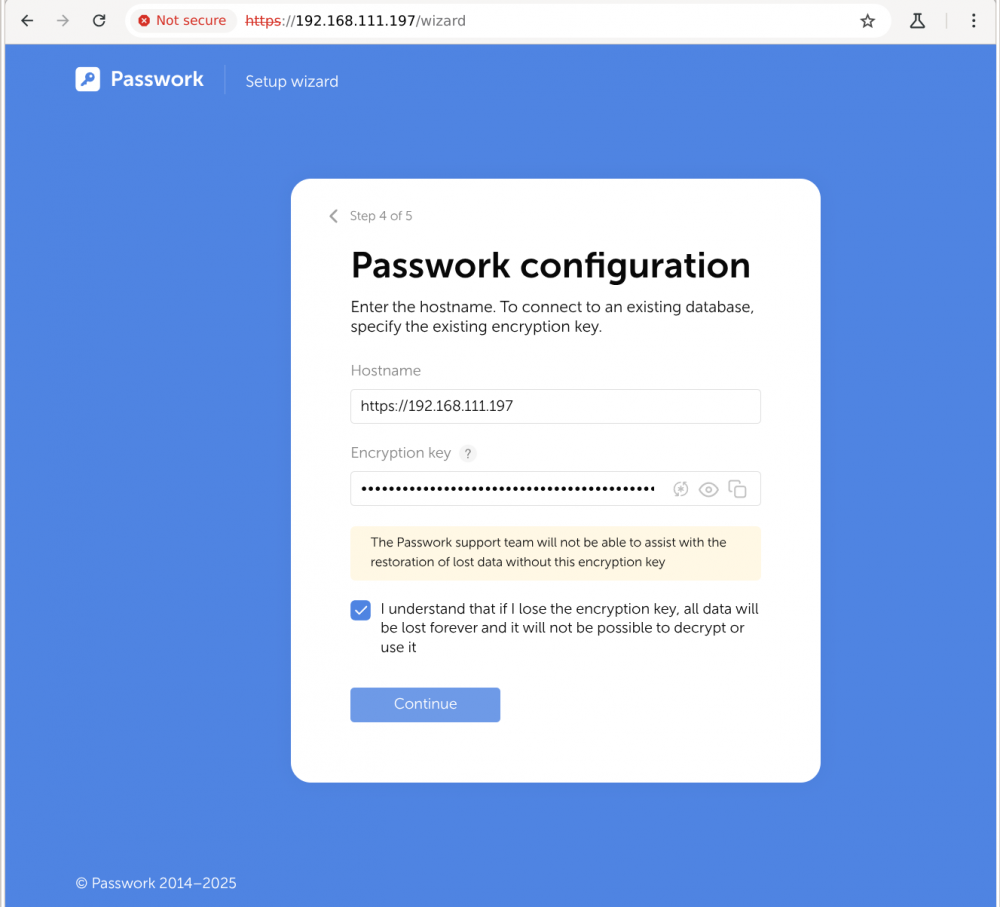
seejärel esitada litsents faili üles laadimise kujul
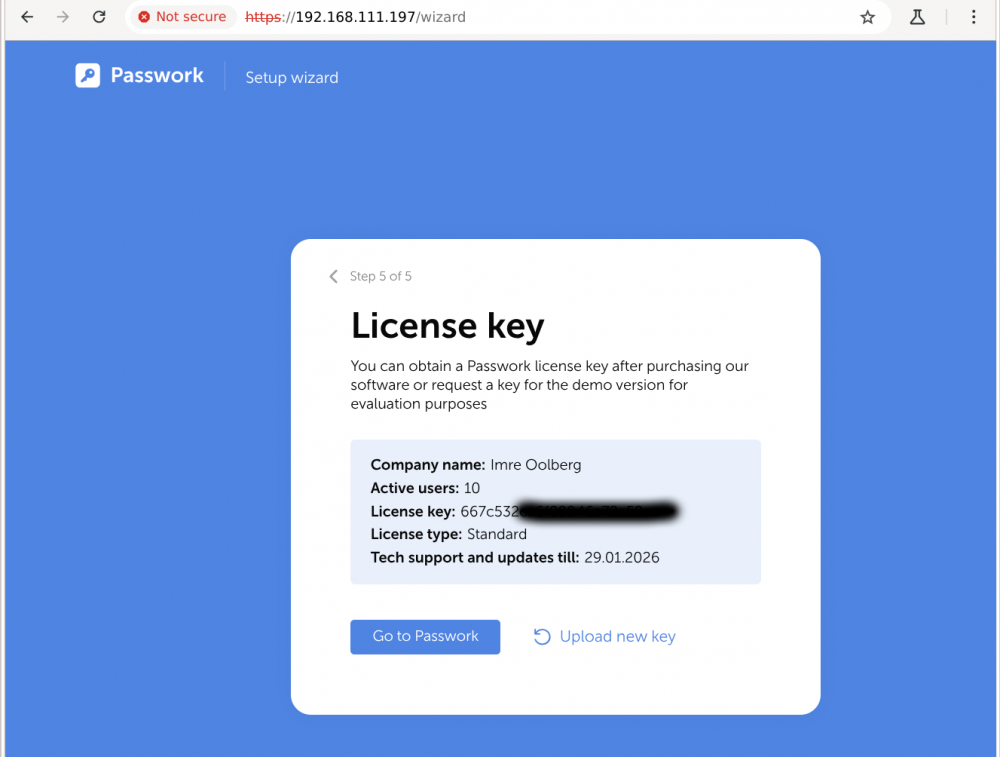
seejärel kirjeldada esimene kasutaja, admin jms privileegidega
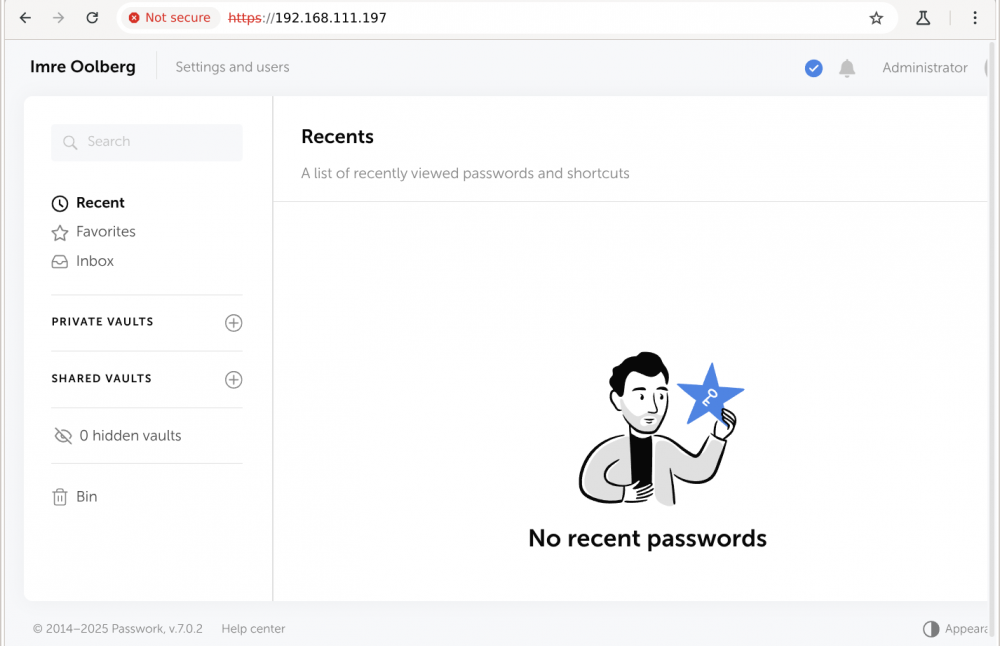
Lõpuks, peale sisselogimist paitsab selline pilt
https:// seadistsamine
https:// iseenesest töötab kohe algupäraselt, aga self-signed vms sertifikaadiga, custom sertifikaadi kasutamiseks sobib tekitada kaks faili
duser@pwrk-01:/srv/passwork$ pwd /srv/passwork duser@pwrk-01:/srv/passwork$ ls -l conf/ssl/fullchain.pem conf/ssl/privkey.pem -rw-r--r-- 1 duser root 3590 Jul 12 20:10 conf/ssl/fullchain.pem -rw------- 1 duser root 1704 Jul 12 20:11 conf/ssl/privkey.pem
ja öelda
duser@pwrk-01:/srv/passwork$ docker compose stop duser@pwrk-01:/srv/passwork$ docker compose start
Tundub, et passwork rakendus sisaldab ise letsencrypt tuge kasutades docker-compose.yml failis, iseasi kui hea mõte on passwork rakendus teha internetist ligipääsetavaks
duser@pwrk-01:/srv/passwork$ head -n 30 docker-compose.yaml
services:
nginx:
..
environment:
- USE_LETSENCRYPT
- DOMAIN
...
Kindlasti on variant pidada eraldi nö sertifikaatide uuendamise nginx serveri ja sealt võtta sertifikaadid ja neid kasutada passwork dockerhostis
# certbot certonly --manual --preferred-challenges=dns --email imre@auul.pri.ee --server https://acme-v02.api.letsencrypt.org/directory --agree-tos --cert-name pwrk.auul.pri.ee -d 'pwrk.auul.pri.ee' --key-type ecdsa
Kasutajate haldamine
- Invite
2FA kasutamine
TODO
Kasutajate keskhaldus - LDAP kataloog
Väärtused
- Server - ldap://192.168.10.125
- Service account -> Distinguished name (DN) - Administrator@dn.moraal.ee
- Service account -> Password - parool
- Service account -> Attribute name for login - samaccountname
ning pressida 'Test' - ootus on vastus 'Successfully logged in'.
Seejärel liikuda lahtri 'DN for finding users in AD/LDAP' juurde ja sisestada
dc=sise,dc=moraal,dc=ee
ja presside 'Refresh users', ootus on näha paneelis 'LDAP users' midagi sellist, '0/47 created'. Pressides View users näeb kataloogi sisu.
smtp teenusega integratsioon
smtp integratsiooni kasutatakse
- invite jaoks
smtp andmete kirjeldamiseks sobib liikuda
System settings -> Email service - Mailer config
ning kasutada nt selliseid väärtusi
- Sender's email - passwork@auul.pri.ee
- TODO
Kasutamine
TODO
Haldusprotseduurid
- varundus ja taaste
- export ja import
Versiooni uuendmine - 7.0.8 -> 7.0.10
Eesmärgil lahendust uuendada, öeldakse kuid tulemusena saab muu hulgas sellise teksti konsoolile
./update.sh .. Backup successful Unable to find image 'alpine:latest' locally latest: Pulling from library/alpine 9824c27679d3: Pull complete Digest: sha256:4bcff63911fcb4448bd4fdacec207030997caf25e9bea4045fa6c8c44de311d1 Status: Downloaded newer image for alpine:latest ./update.sh: line 143: [[: 070008: value too great for base (error token is "070008") No previous version is installed or version is below 070000. Code has been obtained, no need to recreate services during initial install. duser@pwrk-01:/srv/passwork$
kus
- tundub, et süsteem kasutab alpine tõmmist mingiteks abistavateks tegevusteks
Siiski peale
# cd /srv/paswork # docker compose stop # docker compose start
on webgui pealt paista, et kasutatakse v. 7.0.10. Support vastas selle nähtuse kohta, et tarkvara uuendamine õnnestus ja nad kohendavad uuendamise osakonda. Tundub, et uuedamise käigus tõmmiseid endid ei asendatud, aga php konteinerite sees uuendati php rakenduse sisu.
Kasulikud lisamaterjalid
Versiooni uuendmine - 7.0.10 -> 7.2.0
duser@pwrk-01:/srv/passwork$ ./update.sh
Downloading version 070200...
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 23.1M 100 23.1M 0 0 11.7M 0 0:00:01 0:00:01 --:--:-- 11.7M
Verified OK
Successfully checked signature for Passwork archive
WARN[0000] The "UID" variable is not set. Defaulting to a blank string.
WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string.
COMPOSE_PROFILES="local_notify,mongo"
WARN[0000] The "UID" variable is not set. Defaulting to a blank string.
WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string.
2025-11-08T21:51:42.939+0000 writing admin.system.version to archive on stdout
2025-11-08T21:51:42.940+0000 done dumping admin.system.version (1 document)
2025-11-08T21:51:42.941+0000 writing pw.activity_logs to archive on stdout
2025-11-08T21:51:42.941+0000 writing pw.snapshots to archive on stdout
2025-11-08T21:51:42.941+0000 writing pw.tasks to archive on stdout
2025-11-08T21:51:42.944+0000 writing pw.sessions to archive on stdout
2025-11-08T21:51:42.951+0000 done dumping pw.sessions (247 documents)
..
2025-11-08T21:51:43.033+0000 done dumping pw.locks (0 documents)
2025-11-08T21:51:43.034+0000 done dumping pw.ldap_users (0 documents)
Successfully copied 5.76MB to /srv/passwork/backup/
WARN[0000] The "UID" variable is not set. Defaulting to a blank string.
WARN[0000] The "DB_RUN_FLAGS" variable is not set. Defaulting to a blank string.
Backup successful
Container passwork_php Recreate
Container passwork_cron Recreate
Container passwork_php Recreated
Container passwork_nginx Recreate
Container passwork_cron Recreated
Container passwork_nginx Recreated
Container passwork_cron Starting
Container passwork_php Starting
Container passwork_php Started
Container passwork_nginx Starting
Container passwork_cron Started
Container passwork_nginx Started
Waiting for php-fpm and warming up.
Updated to 070200 successfully!
duser@pwrk-01:/srv/passwork$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3aabe1753ca3 passwork/docker-nginx "/entrypoint.sh ngin…" About a minute ago Up About a minute 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp passwork_nginx
eb1fa9a35ad0 passwork/docker-php8.3 "/entrypoint.sh tini…" About a minute ago Up About a minute passwork_cron
fb3a93ec5717 passwork/docker-php8.3 "/entrypoint.sh php-…" About a minute ago Up About a minute passwork_php
ced681df8cfb passwork/docker-postfix "/entrypoint.sh post…" 3 months ago Up 4 minutes 25/tcp passwork_postfix
5c905a145c47 passwork/docker-psmdb6 "/entrypoint.sh mong…" 3 months ago Up 4 minutes 27017/tcp passwork_db
duser@pwrk-01:/srv/passwork$
Seejuures on veider, et jätkuvalt on mongodb versioon 6
duser@pwrk-01:/srv/passwork$ docker exec -it passwork_db mongosh Current Mongosh Log ID: 6914a55f0239271dd7a762f8 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0 Using MongoDB: 6.0.21-18 Using Mongosh: 2.5.0 ...
St just põhjusel, et https://passwork.pro/blog/passwork-7-2/?ref=passwork.pro/blog aadressil tekst 'Release notes of 7.2.0' ütleb
'Important: Passwork requires MongoDB version 7.0 or higher. Earlier versions are not supported and may cause compatibility issues.'
Võib-olla oleks õige sooritada selline järgnevus
- take backup of the virtaul machine of this dockerhost
- export at passwork webgui all content
- shut down system and prepare new clean dockerhost
- do fresh install using 7.2.0 software
- import previosly done export
- little bit of going over some configurations etc
MongoDB v. 6 -> v. 7 uuendamine
FCV väärtuse küsimine
duser@pwrk-01:/srv/passwork$ docker exec -it passwork_db mongosh
Current Mongosh Log ID: 6917a020c571fefa92a762f8
Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0
Using MongoDB: 6.0.21-18
Using Mongosh: 2.5.0
For mongosh info see: https://www.mongodb.com/docs/mongodb-shell/
------
The server generated these startup warnings when booting
2025-11-14T21:31:05.489+00:00: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine. See http://dochub.mongodb.org/core/prodnotes-filesystem
2025-11-14T21:31:05.967+00:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted. You can use percona-server-mongodb-enable-auth.sh to fix it
2025-11-14T21:31:05.967+00:00: vm.max_map_count is too low
------
test> db.adminCommand( { getParameter: 1, featureCompatibilityVersion: 1 } )
{ featureCompatibilityVersion: { version: '6.0' }, ok: 1 }
FCV muutmiseks sobib öelda mongosh promptis
test> db.adminCommand( { setFeatureCompatibilityVersion: "7.0", confirm: true } )
{ ok: 1 }
logis öeldakse
{"t":{"$date":"2025-11-14T21:41:24.292+00:00"},"s":"I", "c":"-", "id":6744302, "ctx":"conn13","msg":"setFeatureCompatibilityVersion succeeded","attr":{"upgradeOrDowngrade":"upgrade","serverType":"replica set/standalone","fromVersion":"6.0","toVersion":"7.0"}}
Versiooni uuendmine - 7.2.3 -> 7.2.4
Tundub, et 7.2.x osakonnas toimuvad mõnda aega uuendused nö ootuspäraselt, st pole vaja tegeleda eraldi andmebaasiga, ei ole muidu tagasilööke jne
duser@pwrk-01:/srv/passwork$ ./update.sh ...
Infoarhitektuur
Väited
- Kõige peamisem andmete salvestamise nö konteiner on 'vault'
- Kasutaja saab vaikimisi moodustada vaultisid, kui ta neis olevatele saladustele ligipääsu teistega ei jaga, jääb vault privaateseks
- Passwork kasutajaid saab organiseerida gruppidesse (user group ehk ug-)
Passwork sisu hieraria on selline
Vault-1 Vault-2
| |
| |
| |
|----- Folder-1-a |---- Folder-2-a
| | | |
| | | |
| |----- Password-1-a-1 | |----- Password-2-a-1
| |----- Password-1-a-2 | |----- Password-2-a-2
| ... | ...
| | ...
|
|----- Folder-1-b
|
|
|----- Password-1-b-1
| ...
|
|----- Password-1-b-2
|
|
|---- Name-1-b-2-a
|---- Login-1-b-2-a
|---- Password-1-b-2-a
|---- URL-1-b-2-a
| ...
|
|---- Name-1-b-2-b
|---- Login-1-b-2-b
|---- Password-1-b-2-b
|---- URL-1-b-2-b
...
- Passwork 'Password' sissekande field on kõige elementaarsem info esinemise element
Kontseptuaalselt võiks passwork lahendust kasutada sellise mõtlemisega
- folderite abil moodustatakse ressrusside parvi (nt rg-infosysteem-yks, rg-infosysteem-kaks, rg-pve, rg-tulemyyr, rg-storage)
- kasutajate gruppide abil moodustatakse kasutajate parvi (nt ug-is-yks-sysadm, ug-is-yks-appadm, ug-is-yks-user, ug-pve-sysadm, ug-storage-sysadm)
- passwork acl süsteemi abil ühendatakse ressurside ja gruppide parvi omavahel kokku
ressursside-infovarade-infosüsteemide paigutamine kolme dimensiooni
- internal vs external dimensioon - kas kasutajad on eranditult haldusüksusest või tegemist on internetti publitseeritud teenusega
- core vs leaf dimensioon - kas tegemist on tuum teenusega, st teenusega mis ei sõltu millestki muust (nt kettakast); või on tegemist paljudest komponentidest sõltuva lahendusega (nt lõppkasutajate teenindav infosüsteem avalikus internetis (sõltub kettakastist, virtualiseerimise platvormist, tulemüürist)
- prod-test-dev dimensioon - kas tegu on toodangu või test kasutusjuhtumiga infosüsteemist
Nt võiks kasutada selliseid vault nimesid
- vlt-core-int-prod - sisemise publiku kasutamiseks tuum ressruss - nt kettakast
- vlt-core-ext-prod - avalikuks kasutamiseks tuum ressurss - sellist kombinatsiooni esineb nö looduses harva
- vlt-leaf-ext-prod - avalikuks kasutamiseks mõeldud infosüsteem - nt mingit sorti wordpress/drupal/mediawiki põhine avalik lahendus
- vlt-leaf-int-prod - sisemiseks kasutamiseks mõeldud infosüsteem - nt ipam halduslahendus
- vtl-leaf-ext-test - avalikuks testimiseks mõeldud infosüsteem - nt mingit sorti wordpress/drupal/mediawiki põhine avalik lahendus
Kusjuures dimensioonidele kombinatsioonidele vastavad erinevad vault'id.
Sellise lähenemise tulemusena on võimalik erinevatele passwork kasutajatele usaldada ligipääse erinevatele ressurssidele suhteliselt üksikajalikult ligipääsemisi kontrollides, nt
- ug-storage-sysadm - storage ressurssidele (füüsilise kettakasti haldusliides, ceph lahenduse node'id) saavad ligi süsteemiadministreerimise tegevuste asjus gruppi kuuluvad kasutajad (ja ega sellise ligipääsuga ei saagi eriti muud toimuda peale süsteemiadministreerimise, nt lun tekitamine, lun group seadistamine, host affinity kirjeldamine)
- rg-storage - storage ressursside gruppi kuuluvad Password sissekanded asuvad vastavas folderis
- kuigi nö tehniliselt saaks anda rg-storage resource-grupile ligipääse nt ug-is-yks-sysadm kasutajatele grupile, vaevalt see on kuigi asjakohane
Esmalt moodustatakse kasutajate grupp, antud juhul on vaatluse all grupp 'ug-pve-sysadm'
- grupis on üks kasutaja, algustähega M
- grupp on seotud ühele vaultile ligipääsemisega
- grupi nime võiks lugeda selliselt, et pve lahendusele soovitakse anda süsteemi-administreerimise alast ligipääsu
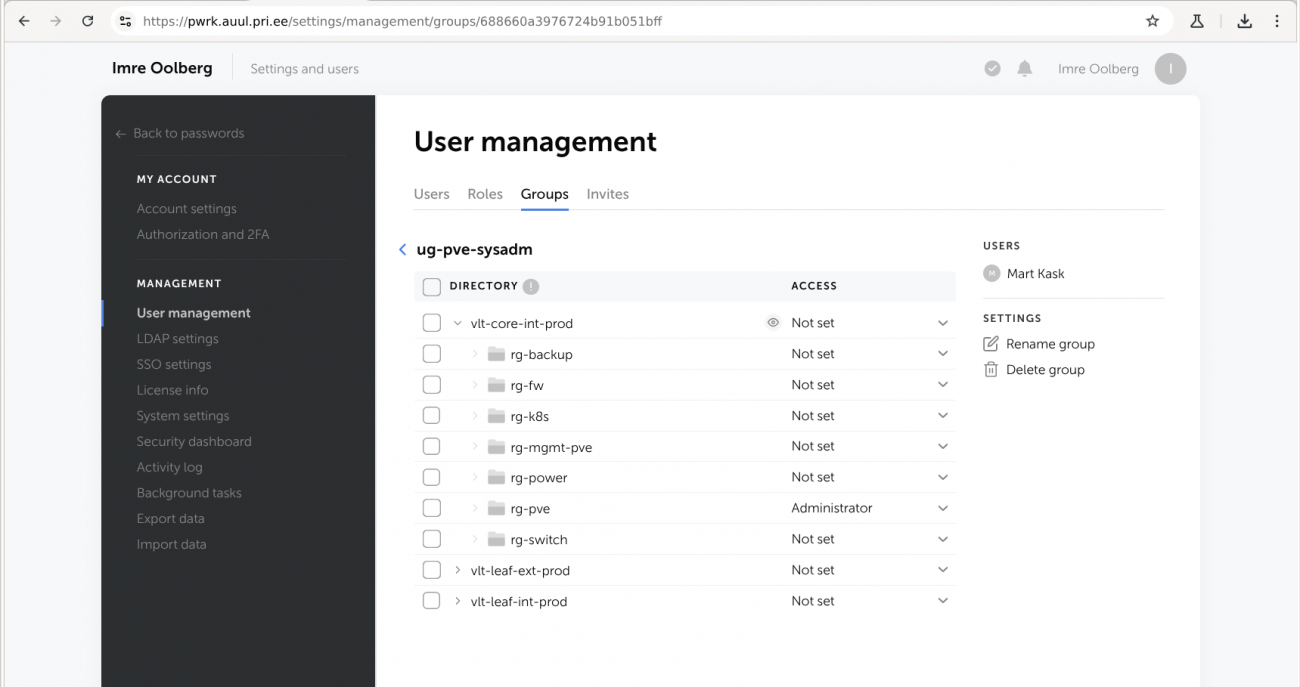
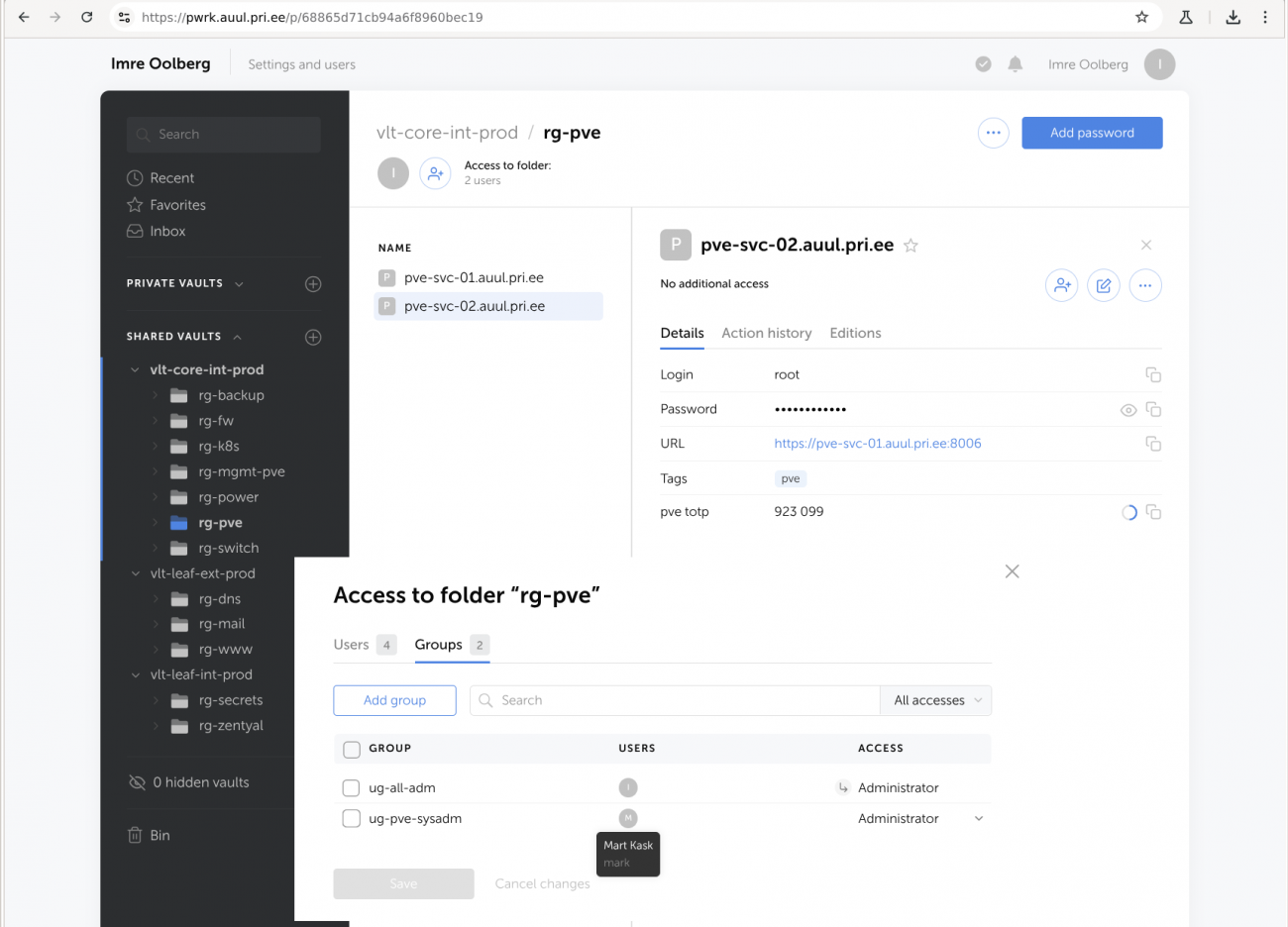
seejärel:
- seostatakse kasutajate grupiga kasutaja Mart Kask - paremal üleval 'USERS'
- seostatakse kasutajate grupiga ressursside grupp 'vlt-core-int-prod -> rg-pve', millele antakse ligipääs tasemel 'Administrator'
Tulemus paistab sedasi
- avatud on ressurside vaates 'vlt-core-int-prod -> rg-pve' osakond, ning Password tüüpi sissekanne 'pve-svc-02.auul.pri.ee'
- sissekande koosseisus on muude field'ide hulgas 'pve totp' nimega field, mille omadus on olla nö google authenticator compatible time-based-on-time-password
- eraldi on lisaks avatud pop-up aken pressides üleval 'Access to folder -> 2 users' peale, kust on näha millise grupp abil on mis privleeg antud
MongoDB
duser@pwrk-01:~$ docker exec -it passwork_db mongosh Current Mongosh Log ID: 6886ca4e9e57fe6db9a762f8 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.5.0 Using MongoDB: 6.0.21-18 Using Mongosh: 2.5.0 For mongosh info see: https://www.mongodb.com/docs/mongodb-shell/ ... pw> show dbs admin 40.00 KiB config 108.00 KiB local 72.00 KiB pw 5.72 MiB pw> test> use pw switched to db pw pw> db.items.countDocuments() 193 pw>
vault andmete küsimine
pw> db.vaults.find({ name: /v-auul/i })
[
{
_id: ObjectId('68729adc05fb74f7b20f9ee6'),
createdAt: ISODate('2025-07-12T17:26:52.534Z'),
creatorId: ObjectId('68729a5c6515f0d969054e06'),
deleted: null,
isSnapshotsMigrated: true,
isUsersMigrated: true,
masterKeyHash: null,
name: 'v-auul',
salt: null,
updatedAt: ISODate('2025-07-12T21:40:47.599Z')
}
]
pw>
Folder info küsimine
pw> db.folders.find({ "name": /rg-pve/i }).pretty()
[
{
_id: ObjectId('68865a19531c35bd9306be7b'),
ancestorIds: [],
createdAt: ISODate('2025-07-27T16:55:53.214Z'),
deleted: null,
name: 'rg-pve',
updatedAt: ISODate('2025-07-27T16:55:53.214Z'),
vaultId: ObjectId('68865953a9c423aa79042ef2')
}
]
pw>
Praktiliselt sisu sissekannetega ei saa sellisel viisil töötada, kuna sisu-andmed on krüptitud.
API kasutamine
Kasutuskoha ettevalmistamine
root@dh-passwork-test:~# apt install python3-venv root@dh-passwork-test:~# su - imre imre@dh-passwork-test:~$ python3 -m venv ~/myenv imre@dh-passwork-test:~$ source ~/myenv/bin/activate (myenv) imre@dh-passwork-test:~$ pip install git+https://github.com/passwork-me/passwork-python.git (myenv) imre@dh-passwork-test:~$ pip list Package Version ------------------ --------- certifi 2025.7.14 cffi 1.17.1 charset-normalizer 3.4.2 cryptography 45.0.5 idna 3.10 passwork-python 0.1.3 pbkdf2 1.3 pip 24.0 pycparser 2.22 python-dotenv 1.1.1 requests 2.32.4 urllib3 2.5.0
API võtme tekitamine
- peale sisselogimist 5 minuti jooksul liikuda kasutaja 'Authorization and 2FA' osakonda
- liikuda sektsiooni 'API tokens' juurde
- pressida Generate ja salvestada kaks saladust, neid on pärast python skriptis tarvis
Kasutamine
$ cat pwrk-02.py
import json
from passwork_client import PassworkClient
client = PassworkClient(host="https://pwrk.auul.pri.ee/")
client.set_tokens("uUQUMutd9VNuAFQ8Vu8RswPDV0JIO0Q+tl1b2uF9jpU=", "lnuTB/xbE3D+VV6b5+/bn+lrTR5A04x7BIVayfx3eG8=")
vault_name = "vlt-test-02"
vault_id = client.create_vault(vault_name)
print(f"Vault was created: {vault_id}")
ning käivitamisel
(myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py Vault was created: 6887d71da0f06ae02f060419
Alternatiiv 'client.create_vault' väljendusele on kasutada 'client.call' kuju, nt on samaväärne eelmisele esitada
..
vault_name = "vlt-test-02"
vault_id = client.call("POST", "/api/v1/vaults", {
"name": vault_name
})
print (vault_id)
...
Olemasolvate vaultide nimekirja saamine
..
vaults = client.call("GET", "/api/v1/vaults")
print(json.dumps(vaults, indent=2))
...
(myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py
{
"items": [
{
"id": "78864af6acf14cf24a0472aa",
"name": "vlt-core-ext-prod",
"hasFolders": true,
"isGranted": true,
"isVisible": true
},
{
"id": "78864af6acf14cf24a0472b9",
"name": "vlt-core-ext-test",
"hasFolders": false,
"isGranted": true,
"isVisible": true
},
..
entry tekitamise näide
import json
from passwork_client import PassworkClient
client = PassworkClient(host="https://pwrk.auul.pri.ee/")
client.set_tokens("uUQUMutd9VNuAFQ8Vu8RswPDV0JIO0Q+tl1b2uF9jpU=", "lnuTB/xbE3D+VV6b5+/bn+lrTR5A04x7BIVayfx3eG8=")
vault_name = "vlt-test-02"
vault_id = client.create_vault(vault_name)
print (vault_id)
folder_id_01 = client.call("POST", "/api/v1/folders", {
"vaultId": vault_id,
"name": "rg-fld-01"
})
print (folder_id_01)
folder_id_02 = client.call("POST", "/api/v1/folders", {
"vaultId": vault_id,
"name": "rg-fld-02"
})
print (folder_id_02)
entry_01 = client.call("POST", "/api/v1/items", {
"vaultId": vault_id,
"folderId": folder_id_02["id"],
"name": "entry_01",
"login": "login_01",
"url": "https://login_01.url/"
});
entry_02 = client.call("POST", "/api/v1/items", {
"vaultId": vault_id,
"folderId": folder_id_02["id"],
"name": "entry_02",
"login": "login_02",
"url": "https://login_02.url/"
});
entries = client.call("GET", "/api/v1/items", {
"vaultId": vault_id,
"folderId": folder_id_02["id"]
});
print(json.dumps(entries, indent=2))
(myenv) imre@dh-passwork-test:~$ python3 pwrk-02.py
6887e42b11d60d12790a962e
{'id': '6887e42bda4e92f70107ca2a'}
{'id': '6887e42b5f680d552109df55'}
{
"items": [
{
"id": "6887e42ba3189a9a790e08ab",
"name": "entry_01",
"folderId": "6887e42b5f680d552109df55",
"vaultId": "6887e42b11d60d12790a962e",
"isDeleted": false,
"login": "login_01",
"url": "https://login_01.url/",
"tags": [],
"color": 0,
"isFavorite": false
},
{
"id": "6887e42ba0f06ae02f060429",
"name": "entry_02",
"folderId": "6887e42b5f680d552109df55",
"vaultId": "6887e42b11d60d12790a962e",
"isDeleted": false,
"login": "login_02",
"url": "https://login_02.url/",
"tags": [],
"color": 0,
"isFavorite": false
}
]
}
(myenv) imre@dh-passwork-test:~$
Kasulikud lisamaterjalid
- https://docs.passwork.pro/api-and-integrations
- paigalduse koosseisus on hea .pdf fail
root@dh-passwork-test:~# find /srv/passwork/ -name \*reference.pdf -ls 1835842 1312 -rw-r--r-- 1 duser duser 1340005 Jul 19 15:10 /srv/passwork/www/070009/files/api-schema/Api\ reference.pdf root@dh-passwork-test:~#
brauseri plugin
Väited
- kõige tavalisem viis passwork kasutamiseks parooli sisestuse olukorras on avatud nt kõrvuti kaks brauserit: 1. passwork kust vaadatakse saladus, 2. veebikoht kuhu pastetakse saladus
- brauseri plugin abil aitab passwork vastata brauseril ligipääsu küsimustele automaatselt (veebikohtade autentimise vorme automaatselt täites, eriti username ja password, vähem totp)
- brauseri plugina aktiveerimisel moodustatakse brauseri ja passwork vahele api key laadse usalduse kasutamise sarnane kontakt
- ühelt poolt on brauseri pöördumise võimekus registreeritud passwork'is
- teiselt poolt on passwork asukoht ja vajalik credential registreeritud brauseris (local storage vms osakonnas)
- passwork kasutamine brauseris kasutada olevate paroolide jaoks ei eelda, et sama brauseriga on passwork rakendusse sisse logitud, st see toimub taustal
brauseri plugina paigaldamine
- https://passwork.pro/user-guides/browser-extension/getting-started
- https://chromewebstore.google.com/detail/passwork-self-hosted/ibiipnmmlnehmeonnhbdajcfagcgihkl
google chrome web store
plugina ühendamine passwork self-hosted lahendusega, Host lahtrisse tuleb kirjutada nt https://pwrk.auul.pri.ee/
Lõpuks öeldakse 'Extension is authorized' (tõenäoliselt küsitakse passwork veebikoha ligipääsu ka). Edaspidi kasutamise ajal ei ole sama brauseriga sisselogimine eelduseks.
brauseri plugina kasutamine
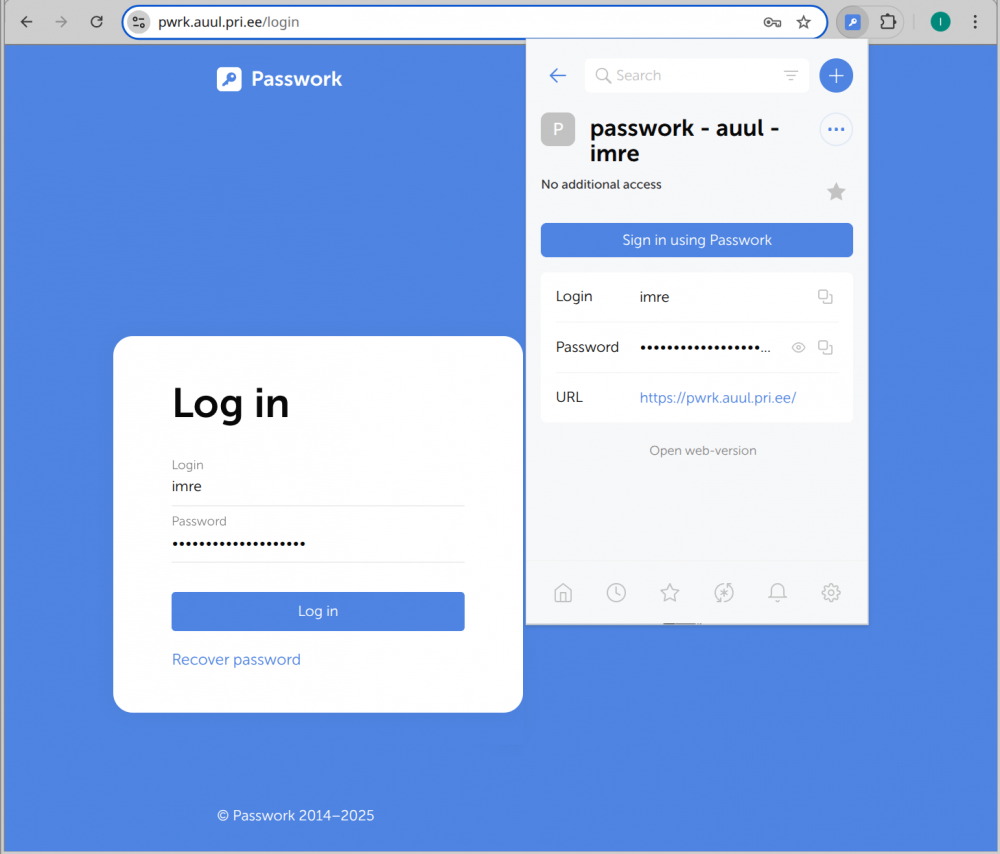
Kasutamine paistab välja selline
kus
- brauseri aadressi real on paremal pluginate-extensionite osakond, eriti passwork lisa
- antud juhul seisneb teravmeelsus selles, et passwork'i logitakse sisse sama passwork abil
brauseri plugina uuendamine
Tundub, et uuendamine toimub MacOS keskkonnas töötava Google Chrome puhul nö automaatselt brauseri enda uuendamise käigus, maksab episoodiliselt üle kontrollida.
Kasulikud lisamaterjalid
- TODO